Preface
Currently, I am playing under 404Unfound, a CTF team formed by my friends and I. More of my writeups can be viewed on the site too!
TISC’23: Disk Archaeology
This was a forensic challenge in TISC, involving the analysis of a disk image. We are provided with a file called challenge.tar.xz which we had to find the hidden flag within the files.
The Challenge
1 | Unknown to the world, the sinister organization PALINDROME has been crafting a |
Unzipping the zip file, we have a challenge.img file. Looking at the file type, we can see that it is a Linux filesystem.
1 | kairos@pop-os:~$ file Downloads/challenge.img |
The Analysis
Knowing that this is a forensics challenge, I checked the strings of the file.
1 | kairos@pop-os:~$ strings -t d Downloads/challenge.img | grep -iE "tisc" |
While it looked like that was the flag, a quick search showed that %s is usually a placeholder for a string in languages like C and C++.
Next, I mounted the file onto Autopsy.
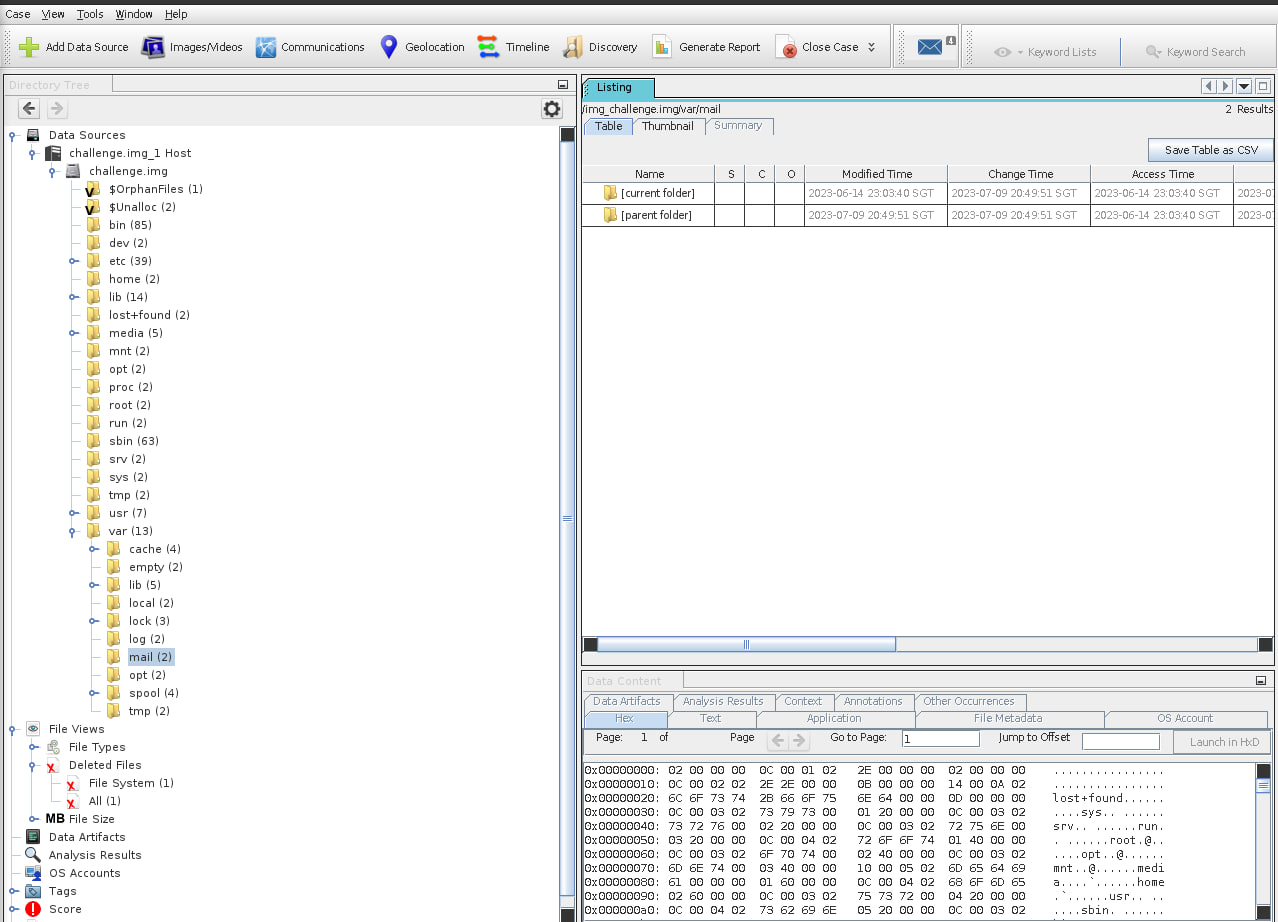
With many different directories and files that we had to potentially dig through, I decided to use Autopsy’s tools to run ingest modules.
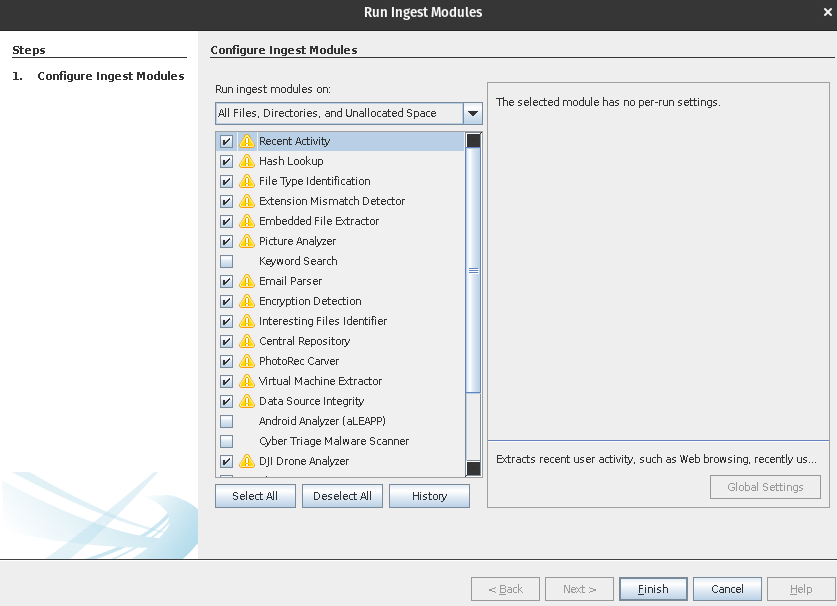
I unchecked the modules that weren’t available (due to compatibility issues with Linux) or irrelevant. These modules helped to carve suspicious files or potential things we could look into.
After running the modules, I was able to retrieve a carved file, f0000008.elf.
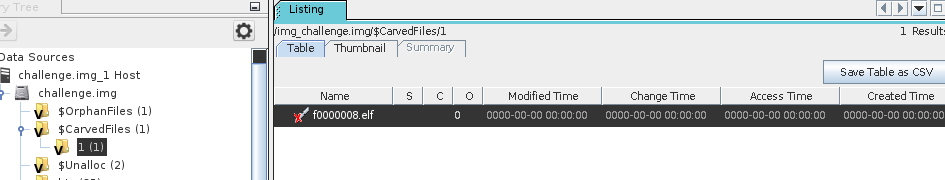
The .elf file format is:
Executable and Linkable Format, a common standard file format for executable files, object code, shared libraries, and core dumps. When you write C code and compile it, the resulting object files are often in ELF format.
Retrieving the file directly through Autopsy, I checked the file information.
1 | kairos@pop-os:~$ file Downloads/f0000008.elf |
I tried to analyse the strings, but did not get any useful information. Hence, I had to dig deeper. Initially, I tried to reverse the binary using binary ninja, but it led me rounds and rounds without any leads :”( and thus I had to find another solution.
The Solution
The first step was to change the permissions of the file to allow it to be executed.
1 | kairos@pop-os:~$ chmod +x Downloads/f0000008.elf |
While it is possible to directly run the file, an error would be thrown if there are missing dependencies (I did not encounter that error, but it was highlighted by a friend).
To check for missing dependencies, ldd (List Dynamic Dependencies) can be used to check the shared library dependencies of the file.
1 | ldd Downloads/f0000008.elf |
To install the missing package,
1 | sudo apt-get install musl |
Next, we can directly run the file now.
1 | kairos@pop-os:~$ ./Downloads/f0000008.elf |
And we got the flag!